
VentureBeat presents: AI Unleashed – An exclusive executive event for enterprise data leaders. Network and learn with industry peers. Learn More
Emerging from stealth today with one of cybersecurity’s largest-ever seed rounds of $51 million, startup Gutsy’s vision is to revolutionize security governance through process mining.
To gain perspective on Gutsy’s sizable funding round, VentureBeat used Crunchbase to analyze all cybersecurity startups that have received seed funding from January 2019 to the present. Of 2,016 startups the average seed round was $3.1 million and the maximum was $181 million. In aggregate, cybersecurity startups raised $4.8 billion in seed funding.
Gutsy’s launch speaks to CISOs’ urgent need for more visibility
The serial entrepreneurs who founded Gutsy include CEO Ben Bernstein co-founder and CEO; VP of R&D Dima Stopel and CTO John Morello. Additionally, the trio were a part of the founding team of Twistlock, a pioneer in cloud-native security that was purchased by Palo Alto Networks in 2019.
“Gutsy’s seed round check was the largest we’ve written, but one of the easiest decisions we’ve made,” said Yoav Leitersdorf, managing partner of YL Ventures, which led the round.
Event
AI Unleashed
An exclusive invite-only evening of insights and networking, designed for senior enterprise executives overseeing data stacks and strategies.
Gutsy’s exit from stealth is well-timed, given how much CISOs are under pressure to quantify the value their investments are making while trimming spending and consolidating their tech stacks to gain greater visibility.
In a survey Gutsy performed on enterprise security governance, 55% of CISOs reported that their security tools are poorly operationalized, which has led to process failure as root cause of 38% of security incidents. Additionally, 63% of audit findings result from breakdowns in security processes.
Process mining has had a successful track record with senior management and boards in helping solve complex problems by reducing roadblocks within and between enterprise resource planning (ERP), supply chain management (SCM) and related systems for years. The process mining market is projected to reach $8.4 billion by 2032, soaring from $1.2 billion in 2022, achieving a compound annual growth rate of 21.5%.
How process mining works
Gartner defines process mining as “a technique designed to discover, monitor and improve real processes by extracting readily available knowledge from the event logs of information systems.” The IT consulting firm notes that process mining includes “automated process discovery, conformance checking, social network/organizational mining, automated construction of simulation models, model extension and repair, case prediction and history-based recommendations.”
Process mining relies on event log data across IT, security and operations systems to quantify current process performance levels and identify where and how bottlenecks and roadblocks occur. Data is extracted from the systems that support a given business process and is correlated across every event, making it possible to visualize an entire end-to-end process and its relative level of performance. Algorithms analyze why and how bottlenecks and roadblocks happen, providing insights into how a process can be improved.
Compliance and cybersecurity are among the most complex processes in an enterprise. But they’re also often the most unknown to IT and security teams due to tool sprawl and conflicting data sources.
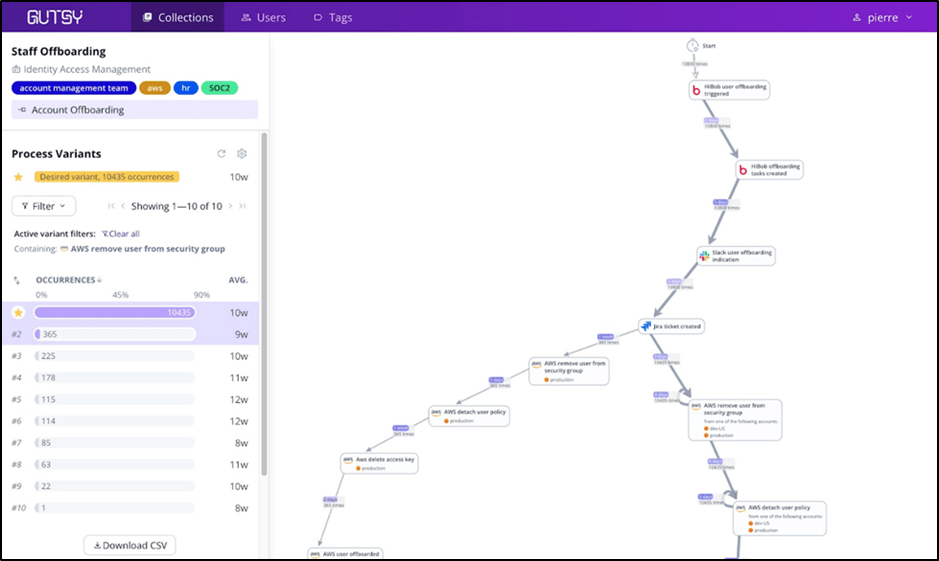
Why process mining is a strong value-add for cybersecurity
Gutsy’s beta, available today, provides three modules covering identity management, incident response and vulnerability management processes. The platform integrates with many tools, including cloud providers, HR systems, vulnerability management tools, ticketing systems, endpoint detection and response (EDR) platforms and more. Gutsy is agentless, provided as SaaS, and is available globally in any customer-selected region.
What makes Gutsy’s approach to solving security governance noteworthy is how the startup has combined process mining with what board members worry about most. A few of these concerns include risk management, security governance and the complex issues of what to insure with which type of cyber insurance.
“Fundamentally, what we’re trying to do is give security leaders an ability to look beyond just the settings and detections they’re getting from the tools and to really understand how and why they are getting those things and where the problems are within the processes they have,” cofounder Morello told VentureBeat.
That’s core process mining and why it’s the go-to technique for troubleshooting process problems across organizations.
Saving valuable time
For CISOs and CIOs and their teams, Gutsy will deliver much-needed visibility into workflows and tool integration, helping to find gaps that many security and IT teams don’t know exist.
That’s good news for teams that are already stretched thin and being asked to rank-order the most and least-valuable cybersecurity and IT tools and eliminate ones that are redundant and offer the lowest ROI. Gutsy’s process mining workflows automatically identify both, helping to curb tool sprawl and allowing organizations to trim maintenance and license renewals.
Morello told VentureBeat that when it comes to automating audits and providing greater visibility, “Gutsy will measure and give them [organizations] visibility into how they’re attaining those things. They’ll literally see the process map that shows every step between all the different teams and tools and technologies.”
VentureBeat’s mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Discover our Briefings.






