
Head over to our on-demand library to view sessions from VB Transform 2023. Register Here
Capitalizing on malware-free tradecraft to launch undetectable breaches, attackers rely on legitimate system tools and living-off-the-land (LOTL) techniques to breach endpoints undetected. Malware-free attacks trade on the trust of legitimate tools, rarely generating a unique signature and relying on fileless execution.
Across all malicious activity tracked by CrowdStrike and reported in their 2023 Threat Hunting Report, 71% of detections indexed by the CrowdStrike Threat Graph were malware-free. A total of 14% of all intrusions relied on remote monitoring and management (RMM) tools based on activity tracked by Falcon OverWatch. Attackers increased their use of RMM tools for malware-free attacks by an astounding 312% year-over-year.
With FraudGPT signaling the start of a new era of weaponized AI and enterprises at risk of losing the AI war, the integration of AI, machine learning (ML) and generative AI into Extended Detection and Response (XDR) needs to be fast-tracked to thwart malware-free and new AI-driven attacks. XDR delivers the consolidation CISOs have been asking for.
XDR improves the signal-to-noise ratio
By relying on APIs and platforms designed to integrate at scale, XDR platforms make the most of every available data telemetry source to detect and respond to potential intrusions and breach attempts in real time. These platforms are proving effective in reducing noise across networks and finding the signals signifying a potential intrusion or attack.
Event
VB Transform 2023 On-Demand
Did you miss a session from VB Transform 2023? Register to access the on-demand library for all of our featured sessions.
XDR is an effective consolidation strategy for CISOs: 96% plan to consolidate their security platforms, with 63% saying(XDR is their top solution choice, according to Cynet’s 2022 survey of CISOs.
Nearly all CISOs surveyed said they have consolidation on their roadmaps, up from 61% in 2021. Gartner predicts that by year-end 2027, XDR will be used by up to 40% of enterprises to reduce the number of security vendors they have in place, up from less than 5% today.
An attribute all XDR leaders have is deep talent density in AI and ML across their teams. Leading XDR platform providers include Broadcom, Cisco, CrowdStrike, Fortinet, Microsoft, Palo Alto Networks, SentinelOne, Sophos, TEHTRIS, Trend Micro and VMWare.
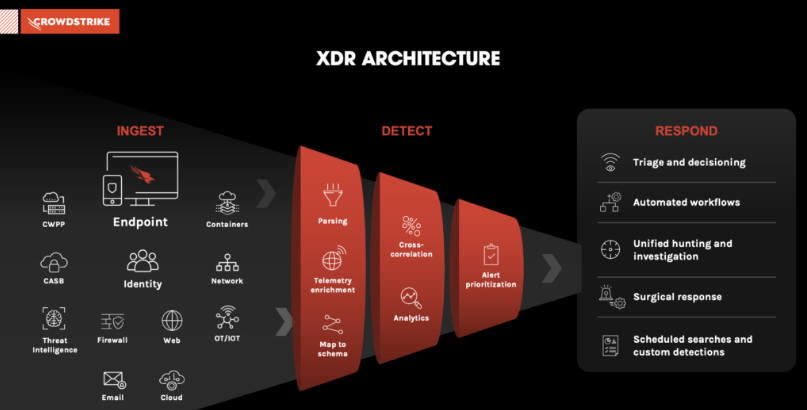
Getting XDR right: Start with endpoints
Endpoints are the stealth on-ramp of choice for large-scale breach attempts: Attackers use stolen identities more than 62% of the time to gain access and are constantly fine-tuning the tradecraft to find gaps in identity and endpoint security, the weakest area of an endpoint.
Insurance, financial services and banking CISOs tell VentureBeat that endpoints are the most challenging threat surface to protect. It’s common for IT and security teams not to know how many endpoints they have, where each endpoint is and its software bill of materials (SBOM). Cleaning up endpoint agent sprawl and automating patch management are the goals many CISOs begin with.
CISOs say it’s common to discover that endpoints are overloaded with agents to the point of being inoperable from a security standpoint. Software conflicts leave endpoints more vulnerable to attack, make them more difficult to manage remotely and can reduce performance.
The Absolute Software 2023 Resilience Index used anonymous telemetry data of its 500 million endpoint devices to see how many endpoints, on average, their customers have. They found that the typical enterprise device has 11 security agents installed, with 2.5 for endpoint management, 2.1 for antivirus/antimalware and 1.6 on average for encryption. Absolute device telemetry data found 67 applications installed on the average enterprise device, with 10% of those devices having more than 100 installed.
Automating endpoint patch management
The CIO of a leading manufacturer told VentureBeat that while patching is always a high priority, she doesn’t have enough staff to keep all patches current. CISO colleagues agree that patch management only gets attention when it’s an emergency — after an intrusion or breach. That conclusion is consistent with Ivanti’s State of Security Preparedness 2023 Report. Ivanti found that 61% of the time, an external event, intrusion attempt or breach reinitiates patch management efforts.
“Patching is not nearly as simple as it sounds,” said Srinivas Mukkamala, chief product officer at Ivanti. “Even well-staffed, well-funded IT and security teams experience prioritization challenges amidst other pressing demands. To reduce risk without increasing workload, organizations must implement a risk-based patch management solution and leverage automation to identify, prioritize, and even address vulnerabilities without excess manual intervention.”
Mukkamala told VentureBeat that he envisions patch management becoming more automated, with AI copilots providing greater contextual intelligence and prediction accuracy.
“With more than 160,000 vulnerabilities currently identified, it is no wonder that IT and security professionals overwhelmingly find patching overly complex and time-consuming,” he said. “This is why organizations must utilize AI solutions … to assist teams in prioritizing, validating and applying patches. The future of security is offloading mundane and repetitive tasks suited for a machine to AI copilots so that IT and security teams can focus on strategic initiatives for the business.”
AI Strengthening XDR resilience with self-healing endpoints
Getting cyber-resilience right in a zero-trust world starts with the endpoint. Boards of directors and the CISOs briefing them say cyber-resilience is now considered a must-have for risk management. Absolute Software’s 2023 Resilience Index reflects the challenge of excelling at the comply-to-connect trend. Balancing cybersecurity and cyber-resilience is the goal.
CISOs tell VentureBeat that self-healing endpoints are the cornerstones of a solid cyber-resilience strategy. Endpoints that heal themselves provide a reliable, real-time stream of telemetry data to train AI and ML models and strengthen XDR platforms. They’re also more difficult to evade and breach compared to their previous-generation constraint and rules-based counterparts. AI and ML-based endpoints detect and respond to potential attacks in milliseconds, which is table stakes for today’s enterprises, given the rapid rise in machine-to-machine attacks.
Leading self-healing endpoint providers include Absolute Software, Akamai, BlackBerry, CrowdStrike, Cisco, Malwarebytes, McAfee and Microsoft 365. VentureBeat has interviewed customers of each vendor and found that Absolute’s approach to being embedded in the firmware of over 500 million endpoint devices is the most reliable in providing SOC teams with the real-time telemetry data they and their XDR platforms need.
Absolute’s approach is unique in its reliance on firmware-embedded persistence as the basis of self-healing, providing an undeletable digital tether to every PC-based endpoint. Absolute Software’s Resilience, the industry’s first self-healing zero trust platform, is noteworthy for its asset management, device and application control, endpoint intelligence, incident reporting and compliance.
XDR: The first line of defense against weaponized AI
The era of weaponized AI is here, and XDR platforms need to step up and take on the challenge of getting all the value they can out of AI and ML technologies if the cybersecurity industry and the many organizations they serve are going to stay safe. No one can afford to lose the AI war against attackers who see the gaps in identities and endpoints as an opportunity to take control of networks and infrastructure.
What’s most troubling is that legacy perimeter-based systems assumed unlimited trust in every identity, endpoint and connection, providing attackers with unchecked access to any system once they compromised an endpoint. Getting XDR right needs to start with endpoints. Cleaning up agent sprawl helps improve endpoint visibility and performance, and automating patch management with AI and ML techniques that learn instead of waiting for the next breach saves IT teams from fire drills and wasted time.
Self-healing endpoints are the cornerstone of cyber-resilience. Getting these areas strong is a prerequisite for making the most of an XDR architecture that can deliver on its potential to protect an organization’s core business functions and customers.
VentureBeat’s mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Discover our Briefings.






